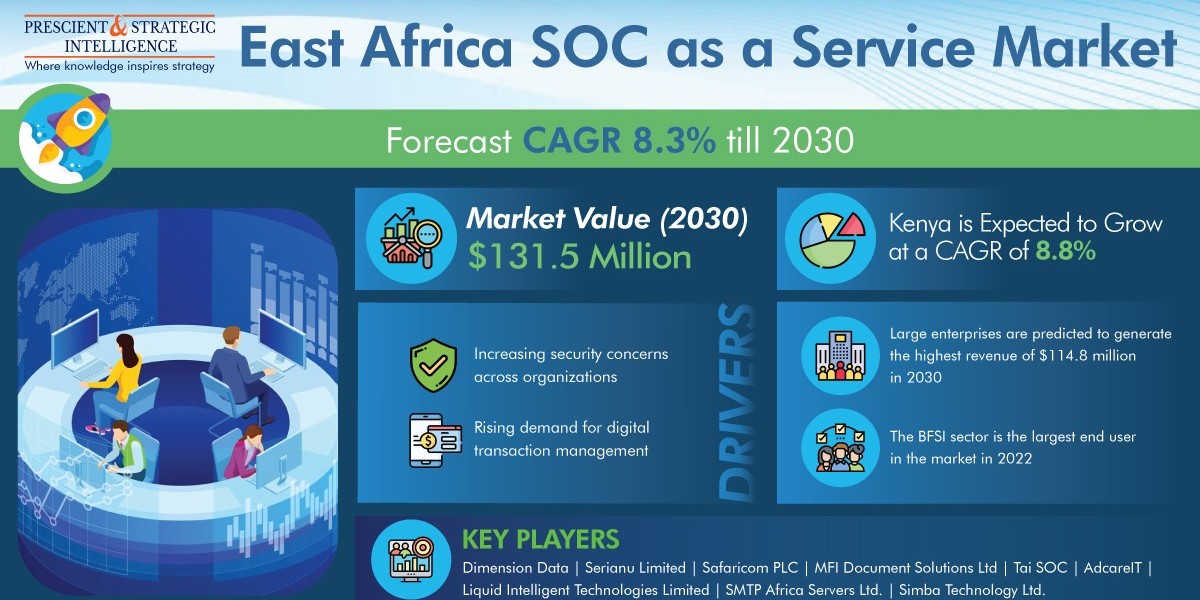
The total revenue generated by the East Africa SOC as a service market was USD 67.8 million in 2022 and it will reach USD 131.5 million by 2030, powering at a rate of 8.3% in the years to come, as stated by a market research firm, P&S Intelligence.
Large enterprises will have the highest revenue of USD 114.8 million in 2030. Furthermore, large enterprises have numerous operations; therefore, they are continuously implementing developed technologies for detection, prevention, and responding, to any type of cyberattack.
Also, MNCs have extensive corporate networks and numerous revenue streams, so they implement SOC as a service solution, the key factor powering the industry.
BFSI sector is the major end user in the recent past, as it is one of the utmost attractive targets for cybercriminals because of its business nature. Characteristically, a worker of a financial service organization gets access to approximately 11 million files on the very first day of work. This number increases to 20 million files for the people working in large companies.
Also, over 70% of cyberattacks are targeted at the financial industry. For instance, over 30 billion accounts will be breached by 2030. The companies operating in the industry are prone to phishing attacks, which sustain the cost of about USD 6 million on every data breach.
Kenyan East Africa SOC as a service market will touch USD 59.1 million by 2030 from USD 29.4 million in 2022, progressing at a rate of 8.8%. in the years to come This is chiefly because of the increasing acceptance of SOC as a service in the retail, BFSI, telecom, IT and, and healthcare industries.
Furthermore, the increasing cases of cybercrimes, organized online threats, increasing ransomware, and escalating number of end users’ system hijacking are generating the demand for SOC as a service in the country . For example, as per an Interpol report, from January 2020 to February 2021, Kenya had 72 million cyberattacks.
In business procedures, log management is frequently put to use for handling data from a source. Characteristically, it deals with log messages created by computers, as well as audit records, audit trails, and event logs, amongst others. For providing more apt results, it regularly gathers and systematizes the data. Furthermore, it acts as a security control for all systems and network logs and is mostly helpful because of its ability to identify cyber threats, security flaws, and criminal activities.
It is due to the increasing security concerns across various organizations, the demand for SOC as a Service in East Africa will continue to increase in the years to come.